Height Cloud

What is cloud security and why is it important ?
Cloud security is a critical aspect of modern computing, given the increasing reliance on cloud-based systems and data storage. It involves a comprehensive set of technologies, procedures, policies, and controls designed to safeguard cloud environments. The importance of cloud security stems from the vast amount of sensitive data stored in the cloud and the potential risks associated with unauthorized access or data breaches. Cloud security encompasses various elements that work together to ensure the safety and integrity of cloud-based resources. These include encryption, identity and access management (IAM), intrusion detection systems (IDS) and intrusion prevention systems (IPS), data loss prevention (DLP), and security information and event management (SIEM). The significance of cloud security can be understood through several key points: data protection, compliance requirements, business continuity, trust and reputation, and risk management. To effectively manage cloud security, several key aspects must be addressed: data encryption, access controls, regular audits, security updates, and education and training. In conclusion, cloud security is essential for protecting valuable data, maintaining compliance, ensuring business continuity, and preserving the trust and reputation of an organization. As cloud computing continues to grow, so does the need for robust security measures to safeguard against evolving threats.

How do you manage risks associated with working at height in construction ?
Managing risks associated with working at height in construction requires proper risk assessment, use of appropriate equipment and tools, worker training, implementation of control measures, and ongoing monitoring and review of safety measures. By following these strategies, you can help ensure the safety of workers and prevent accidents while working at height.

How do data protection regulations apply to cloud computing services ?
**Data Protection Regulations in Cloud Computing Services** Data protection regulations govern the collection, storage, processing, and transmission of personal information to protect individuals' privacy rights. These regulations apply to all organizations that process personal data, including those offering cloud computing services. Cloud service providers must ensure their services meet specific requirements under data protection regulations, such as data minimization, security, transparency, portability, and accountability. The application of these regulations to cloud computing services enhances security, improves trust, and increases transparency but also presents challenges like complexity, cost, and interoperability. As cloud computing services grow, understanding and complying with data protection regulations is crucial for both providers and users to protect personal data effectively.

What is the significance of communication protocols in cloud computing ?
In the realm of cloud computing, communication protocolsIn the realm of cloud computing, communication protocols role in facilitating communication protocols play a pivotal role in facilitating seamless and efficient data exchange between various components of a cloud infrastructure. These protocols ensure that data is transmitted reliably and securely across different platforms, devices, and applications within the cloud ecosystem. This article delves into the significance of communication protocols in cloud computing by highlighting their key functions and benefits.

**What third-party apps integrate well with iCloud for productivity and management ?
The article discusses the best third-party apps that integrate well with iCloud, a cloud storage service provided by Apple Inc. The apps include Evernote, Microsoft Office Suite, Adobe Creative Cloud, Todoist, and Trello, which allow users to store their data on iCloud Drive and access it from any device running these apps. These apps provide features like creating and organizing notes, saving web clippings, capturing ideas, saving documents, collaborating on documents in real-time, storing creative projects, working on projects offline, creating tasks and setting reminders, organizing tasks into projects and sections, creating boards and adding cards representing tasks or ideas, and assigning cards to team members. Overall, these apps make it easy for users to collaborate on projects with others in real-time and manage their tasks from anywhere.

What is the difference between cliff diving and high diving ?
The article discusses the differences between cliff diving and high diving, two sports involving athletes jumping from heights into water. The differences are explored in terms of equipment, techniques, safety measures, and competitive formats. Cliff diving takes place on natural or artificial platforms overlooking bodies of water, with heights ranging from 20 to 27 meters. High diving, on the other hand, occurs on elevated platforms built specifically for competitions, with standardized heights of 10 meters for men and 5 meters for women. Cliff divers must navigate uneven terrain and deal with varying wind conditions, while high divers have a clear path to the edge of the platform. Cliff diving often involves complex rotations and somersaults, while high diving focuses on precision and execution. Safety measures for cliff diving include sufficient water depth, clean water quality, and emergency procedures, while high diving requires regulation-sized pools with adequate depth and space, regular maintenance, and supervision by lifeguards and medical personnel. Competitive formats for cliff diving include individual competitions and team relays, while high diving features individual, synchronised, and team events at various levels such as national, continental, and world championships.

Where can I go for the ultimate zip-lining experience ?
Zip-lining is a thrilling activity that allows you to soar through the air while taking in breathtaking views of your surroundings. If you're looking for the ultimate zip-lining experience, there are several destinations around the world that offer unique and unforgettable experiences. Here are some of the top spots for zip-lining enthusiasts: 1. Arenal Volcano, Costa Rica - Spectacular views of the active volcano and surrounding rainforest, longest zip line course in Latin America, night zip-lining tours available. Must-try experiences include Canopy Tour, Waterfall Rappel, and Night Tour. 2. Cape Tribulation, Australia - Scenic coastal views along the Great Barrier Reef, unique wildlife encounters, thrilling beach landings. Must-try experiences include Rainforest to Reef Tour, Sunset Tour, and Jungle Surfing. 3. Maui, Hawaii - Panoramic views of the Pacific Ocean and lush valleys, multiple courses ranging from beginner to advanced levels, optional ATV tours to reach higher elevations. Must-try experiences include Haleakala Sunrise Tour, Ultimate Rappel & Zip Line Tour, and King Kapu Kini Road Course. 4. Chiang Mai, Thailand - Verdant landscapes dotted with ancient temples, opportunities to spot rare wildlife like gibbons and flying squirrels, family-friendly options available. Must-try experiences include Flight of the Gibbon, Elephant Interaction Tour, and Cultural Workshops. 5. Monteverde Cloud Forest Reserve, Costa Rica - Misty cloud forest environment rich in biodiversity, suspension bridges and zip lines integrated into the natural landscape, eco-tourism at its finest. Must-try experiences include Sky Trek, Canopy Tour, and Night Walk.

What are the latest trends in cyber security ?
The text discusses the latest trends in cyber security, highlighting the following key points: 1. Ransomware attacks are becoming more frequent and can cause significant downtime and financial losses for businesses. Prevention is essential, with regular backups and employee training being crucial components of a robust defense strategy. 2. As more businesses move their operations to the cloud, ensuring the security of cloud-based systems has become a major concern. Cloud providers typically offer a range of security measures, but it is up to individual businesses to ensure that these measures are properly implemented and maintained. 3. The proliferation of connected devices has created new opportunities for cybercriminals to launch attacks. Many IoT devices lack adequate security features, making them easy targets for hackers looking to gain access to networks or steal sensitive data. 4. AI and ML technologies are becoming increasingly important tools in the fight against cybercrime, helping organizations identify and respond to potential threats more quickly and effectively than ever before. However, these technologies also create new opportunities for attackers to launch more sophisticated attacks or evade traditional defenses.

Which tech companies are leading the market ?
This article discusses the leading tech companies in the market, including Apple Inc., Microsoft Corporation, Amazon.com, Inc., Alphabet Inc. (Google), and Facebook, Inc. It highlights their key products and services, such as Apple's innovative devices, Microsoft's software and cloud services, Amazon's e-commerce platform and AWS, Google's search engine and Android OS, and Facebook's social media platforms and advertising revenue. The article also notes the competitive nature of the tech industry and the potential for new leaders to emerge in the future.
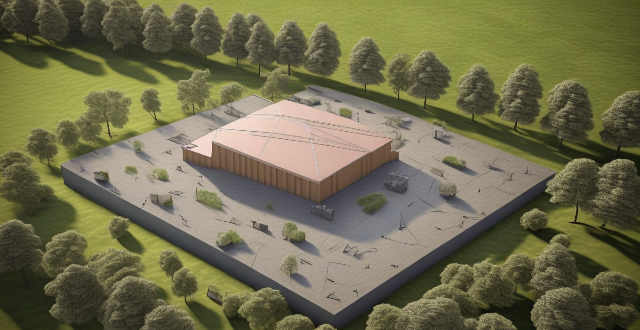
What is the range of a typical communication base station ?
The typical communication base station, also known as aThe typical communication base station, also known as a specific geographic area with wireless The range of a base station can vary based on the type of technology used, the height and location of the tower, and the surrounding environment. Different technologies have different range capabilities, with newer ones like 4G and 5G offering greater coverage and capacity than older technologies like 2G. Tower height and location also play a significant role in determining its range, with taller towers covering wider areas and being less affected by signal blockage. The surrounding environment, including urban or rural areas, can impact the range of a base station. The typical range of a base station can be from a few hundred meters to several kilometers, with practical ranges often being smaller due to interference and other factors. Network operators may use multiple base stations and other techniques to optimize coverage and capacity within their service areas.

How can I upgrade the storage capacity of my iPhone ?
How to Upgrade the Storage Capacity of Your iPhone If you're an iPhone user, you might have encountered the issue of running out of storage space. This can be frustrating, especially when you want to take more photos, download more apps, or save more files. Fortunately, there are several ways to upgrade the storage capacity of your iPhone. Here are some options: Use iCloud - Back up your data: Before upgrading your storage, make sure to back up your data to iCloud. This will ensure that all your photos, videos, and other files are safely stored in the cloud. - Upgrade your iCloud storage plan: Once you've backed up your data, you can upgrade your iCloud storage plan. Apple offers various plans ranging from 50GB to 2TB. You can choose the one that best fits your needs. Use a third-party cloud service - Choose a reliable cloud service: There are many third-party cloud services available, such as Dropbox, Google Drive, and OneDrive. Choose one that you trust and feel comfortable using. - Upload your files: Once you've chosen a cloud service, upload your files to it. This will free up space on your iPhone and allow you to access your files from anywhere. Delete unnecessary files - Check your storage usage: Go to Settings > General > iPhone Storage to see how much space each app and file is using. This will help you identify which items are taking up the most space. - Delete unused apps and files: If you find apps or files that you no longer need, delete them to free up space. You can also offload unused apps without deleting them completely. Transfer your photos and videos - Use iCloud Photos: If you have iCloud Photos enabled, your photos and videos will automatically be stored in iCloud. This will free up space on your iPhone. - Transfer photos and videos to a computer: If you don't want to use iCloud Photos, you can transfer your photos and videos to a computer using iTunes or Finder. This will also free up space on your iPhone. Upgrade to a newer iPhone model - Consider upgrading: If you find that you consistently run out of storage space, it might be time to consider upgrading to a newer iPhone model with more storage capacity. - Trade in your old iPhone: You can trade in your old iPhone for credit towards a new one. Check with your carrier or Apple's website for more information on their trade-in programs.
Are there any age or health restrictions for going on a space travel adventure ?
There are age and health restrictions for going on a space travel adventure. The minimum age is usually 18 years old, while the maximum age varies between providers. Health restrictions include physical fitness tests, mental health evaluations, chronic conditions exclusions, pregnancy prohibitions, recent surgery or injury waiting periods, height restrictions, motion sickness considerations, allergies to materials used in spacecraft construction or supplies carried on board, and drug use disqualifications. These restrictions help ensure the safety and well-being of all participants involved in this exciting but challenging endeavor.

How many communication base stations are needed to cover a city ?
This article discusses the factors affecting the number of communication base stations required for a city, including city size and population density, topography, and building height. It also provides an estimate formula to calculate the number of base stations needed based on city area and coverage per station. The conclusion emphasizes the importance of considering these factors in network planning and deployment to ensure reliable communication services across the city.

Is it possible to upgrade the storage capacity of an older iPhone model ?
Upgrading the storage capacity of an older iPhone model is not possible due to hardware and software limitations. The storage on iPhones is soldered onto the motherboard and encrypted, making it difficult to remove and replace. Additionally, upgrading the storage might require a newer version of iOS that is not compatible with the older device, leading to software issues. Alternative solutions for managing storage effectively include deleting unused apps, clearing cache, using cloud storage services like iCloud, and regularly backing up and resetting the device to factory settings. These methods can help alleviate storage issues and make the most out of the available space.

Can I upgrade the storage capacity of my iPhone without losing any data ?
Upgrading the storage capacity of an iPhone without losing any data is possible but risky. Options include official Apple upgrades, third-party repair services, and using cloud storage. Risks include data loss, voided warranty and insurance, compatibility issues, and high costs. It is recommended to carefully consider the potential risks before attempting a storage upgrade.

How do I properly store a fire extinguisher ?
Proper storage of a fire extinguisher is crucial for its effectiveness and safety. Here's a summary of the key steps: 1. Choose the right location by ensuring visibility, proximity to an exit, and avoiding obstructions. 2. Mount the fire extinguisher using specific brackets at a comfortable height while maintaining a horizontal position. 3. Maintain accessibility by ensuring a clear path and considering signage to indicate its location. 4. Conduct regular maintenance through monthly checks, pressure gauge verification, expiration date monitoring, and hose/nozzle inspections. 5. Avoid improper storage conditions such as temperature extremes, direct sunlight, and wet or humid areas. By following these guidelines, you can ensure that your fire extinguisher is stored correctly and ready for use in emergencies.

How will 5G change the entertainment industry ?
The advent of 5G technology is set to revolutionize various sectors, including the entertainment industry. With its faster speeds, lower latency, and increased connectivity, 5G promises to transform how content is created, distributed, and consumed. In this article, we will explore the potential changes that 5G can bring to the entertainment industry. One of the most significant changes that 5G will bring to the entertainment industry is an enhanced streaming experience. With 5G's faster download and upload speeds, users can enjoy high-quality video and audio content without buffering or lag issues. This means that viewers can watch their favorite movies, TV shows, or live events in real-time, with no interruptions. Moreover, 5G's low latency ensures that there are minimal delays between the broadcaster and the viewer, making it ideal for live streaming events such as sports games or concerts. Another area where 5G can have a profound impact is in virtual reality (VR) and augmented reality (AR) experiences. These technologies require high bandwidth and low latency to function effectively, which makes them perfect candidates for 5G networks. With 5G's capabilities, VR and AR experiences can become more immersive and realistic than ever before. For example, users could attend virtual concerts or sporting events from the comfort of their homes, feeling as if they were actually there. Additionally, AR applications could be used to enhance traditional media by adding interactive elements to books, magazines, or even billboards. Cloud gaming is another area where 5G can make a significant difference. With 5G's fast speeds and low latency, gamers can play high-quality games without needing powerful hardware devices. Instead, they can stream games directly from the cloud, using their smartphones, tablets, or even smart TVs as controllers. This means that gamers no longer need expensive consoles or PCs to enjoy their favorite games; they only need a stable internet connection and a compatible device. Moreover, cloud gaming opens up new opportunities for developers to create more complex and immersive games without worrying about hardware limitations. Finally, 5G can also enable more interactive content creation and consumption. With 5G's increased connectivity and faster speeds, creators can produce interactive videos, podcasts, or other forms of media that allow viewers to engage with the content in real-time. For example, viewers could participate in polls or quizzes during live shows or interact with characters in a movie through AR features on their devices. This level of interactivity not only enhances the viewing experience but also creates new opportunities for advertisers looking to reach engaged audiences.

What are the latest trends in network security protection ?
Network security is a crucial aspect of modern computing, and it's constantly evolving to keep up with new threats. Here are some of the latest trends in network security protection: - AI and ML are becoming increasingly popular for detecting and responding to cyber threats. - IoT devices have poor security features or lack them altogether, making them easy targets for hackers. - With more businesses moving to the cloud, ensuring data is secure is essential. - Threat intelligence involves collecting information about potential threats and using it to improve defenses. - The zero trust model assumes that no one should be trusted by default, including those within an organization's network.

Which country offers the most thrilling bungee jumping spots ?
Bungee jumping is an extreme sport that involves jumping from a tall object while connected to a large elastic cord. Here are some countries that offer the most thrilling bungee jumping spots: - New Zealand: Nevis Bungy and Kawarau Bridge Bungy - United States: Verruckt Waterslide and Stratosphere Tower - South Africa: Bloukrans Bridge and Gouritz River Bungy - Canada: Capilano Suspension Bridge and WildPlay's Mica Slate Quarry - Australia: Cairns Bungy and AJ Hackett Impact Bungy Each country has its unique bungee jumping experiences, and it's up to you to choose which one suits you best.

What are some undervalued tech stocks worth considering ?
Tech stocks are popular but not all are equal; some may be undervalued, presenting a great opportunity for investors. This article discusses four such stocks: Cloudflare, Palo Alto Networks, Twilio, and Zscaler. These companies have seen strong growth and have large addressable markets, yet their stock prices have been relatively flat since their peaks in 2019-2021. They offer potential bargains for investors looking for value in the tech sector.